|
|
I dared suggest that everyone be given clear title to one's personal data. I go as far as to include the history of my past transactions within my confidential profile. While I recognize that organizations with which I interact need an extract of my profile to process any ensuing transaction, I deny them the right to reuse it beyond its fulfillment without my explicit consent. If they go ahead and do it nonetheless, I call it embezzlement.
Meanwhile I protest that security and economic imperatives should not be ignored. Fair minded readers may well wonder if I have painted myself into a corner.
Why not take a real life example and see how it could be done ? How about the recent spat between the US and the EU relative to access to airline passenger data as reported by Nicola Clark and Matthew W. Wald (*) as well as Sarah Laitner, Doug Cameron and Michael Peel (**)? If you think of the numbers involved, more than 10 millions travellers per year, more than 30 profile items collected per traveller, the preemptive transfer of such confidential information from the EU to the US is of biblical scale.
But allow me first to share a story with you. Back in the Age of Enlightenment, a squire went to visit his neighbor, known for his well stocked library. After the required polite talk, the squire asked to borrow a book, to which his neighbor readily assented but on one condition. The squire could read the book to his heart's content as long as he did not leave the library. The squire refused to be put off by this, although the story does not tell if he enjoyed the book as much. A few months later there happened a spate of inclement weather during which the neighbor had the misfortune to break his bellows. He quickly went to the squire's manor to ask whether he could borrow one. At this request, the squire beamed back and declared his neighbor most welcome to use his spare bellows as long as he did not take it off the premises.
.
|
|
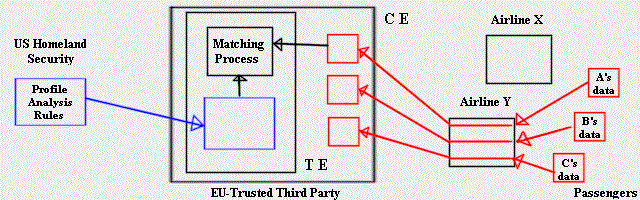
Imagine then the following solution. With the explicit consent of passengers, the airlines submit the required data to an independent service provider trusted by the EU so as to get proper authorization from the US Government. On behalf of the passengers, this third party sets up a confidential environment (CE) to which the US Government sends its profile analysis rules. In such an environment (1):
- "supplier" rules and "user" data can flow in
- rules from one "supplier" can perform any processing on the data of one "user"
- but no output from such a "match" can possibly flow out to the "supplier" unless the "user" gives explicit consent, one data item at a time.
In the case at hand the output is simply a landing authorization by the US Goverment to a passenger, who will indeed want the US Government to know about it when granted. Notice that airlines, acting as relays, whould not be burdened with any processing or archival tasks. Nor shall I add would they be allowed to reuse the information for their own benefit.
In practice one can hardly expect the US Government to trust its profile analysis rules to such a third party. Even if this highly confidential information is encrypted in transit, it must be decoded for execution. Imagine then further that the US Government sets up a tamper-resistant subsystem (TE) within CE for storing and processing the rules (2). While CE continues to ensure the confidentiality of passenger data, the role of TE coupled with regular inspections is to guarantee that any attempt to observe or corrupt the US rules during processing would quickly become apparent.
This "two concentric black holes" architecture (3) do satisfy the requirements of both border security and passenger confidentiality without trading one for the other. Yet I do not imagine a second it will be adopted. For bringing a true solution (4) to the issue currently raised by the US and the EU would cast light on four more issues inherent to pattern recognition science, issues which many would rather not talk about in public (5):
- what is the real purpose of the US Government ?
- pattern classification (detecting whether a specific passenger is a threat based on rules known to the US Government)
- or pattern learning (building and studying a data sample to find effective detection rules)
Because the two black holes architecture is great for detecting (akin to reading the book in the story) but not for learning (akin to using the bellows), the question cannot be avoided.
Of course pattern learning means to take passengers unwittingly on a fishing expedition, a behavior called harassment.
.
- assuming threat detection is the goal, what happens to the false positives, the law-abiding passengers mistakenly labeled as security risks ?
No matter how good, pattern classification always generates false positives (e.g. see my fillip of 05/16/06 ). There should be clear, public policies to compensate for these errors, including something of value besides apologies (6).
.
- what happens to the true positives, the actual terrorists ? Should they:
- (a) get interrogated as they land in the US
- (b) reported to the US, denied entry and subjected to the scrutiny of the EU
- (c) or should they be denied entry but otherwise not reported and let go ?
As a frequent flyer myself, I would prefer true positives to be dealt with appropriately before they board the plane rather than after they land in the US, just in case their plan was to act en route.
But this outcome (b) requires two conditions which go to the heart of the matter:
- passengers would be asked their consent for reporting their landing authorization status to the US and local EU government before knowing whether this status is positive or not
- the US and the EU police and justice authorities would have to agree on procedures
.
- and finally how should the process be funded ?
Since the service would not be imposed on a party already engaged in commerce, such as the airlines or airports, associated costs would have to be financed through some extra taxes and fees. This is certain to focus attention on economic efficiencies:
- should the third party retain historical data, a measure supported by the proposed architecture but at a significant increase in archival costs ?
- how stringent the detection rules should be, knowing that the fewer false negatives (terrorists granted admission), the higher false positives and their associated costs ?
Separating the wheat from the weeds planted by the enemy is never trivial. Rushing to the wrong solution is not the correct answer either.
Philippe Coueignoux
- (*). Hurdle for U.S. In Getting Data On Passengers, by Nicola Clark and Matthew L. Wald (New York Times) - May 31, 2006
- (**) EU airline ruling puts terror deal in doubt, by Sarah Laitner, Doug Cameron & Michael Peel (Financial Times) - May 31, 2006
- (1) for a description of a Confidential Environment, see US Patent 6,092,197 by Coueignoux
- (2) for an example of a Tamper-resistant Environment, see US Patent Application 2004/0133793 by Ginter & alii
- (3) see US Patent Application 2006/0053279 A1 by Coueignoux
- (4) more likely EU governments may invoke their power on security issues to get around the EU privacy laws, burying the issue raised by the EU parliament. See: A sensible judgement on transatlantic trouble, editorial column (Financial Times) - June 2006
- (5) for an inspired call to action, read: A privacy fiasco that needlessly undermines our security, by Richard Falkenrath (Financial Times) - June 2006
- (6) e.g. compensation for losing one's seat to overbooking by airlines may include free travel, free hotel nights and cash awards.
|
|
May 2006 |